The emergence of modern cyber threats directly related to the cryptocurrency sphere is a logical result of the growing popularity and rapid boost in virtual money prices. The information security industry is also improving, enabling users to prevent malware from infiltrating devices effectively.
There are high-quality tools for protecting and checking computers in order to quickly detect viral algorithms, including programs for hidden mining. We will talk about cryptojacking and its types and explain how to prevent cryptojacking while being in a decentralized land.
Table of Contents
- What Is Cryptojacking?
- How Does Cryptojacking Work?
- Cryptojacking via Websites and Emails
- Cloud Cryptojacking
- Cryptojacking via Mobile or Desktop Applications
- Is Cryptojacking a Crime?
- Cryptojacking Examples & Malicious Crypto Mining News
- How to Detect Cryptojacking Malware on Your Computer or Mobile Device
- Monitor Performance
- Scan for Malware
- How to Prevent Cryptojacking
- Antivirus Software
- Browser Extensions Designed to Block Cryptojacking Scripts
- Ad Blockers
- Disable JavaScript
- How Prevalent Are Cryptojacking Attacks?
- Final Thoughts
What Is Cryptojacking?
Cryptojacking is a type of malicious intervention into one’s computer or mobile device in order to use its computer processing power for cryptocurrency mining.
Using different fraudulent methods of intervention, bad actors implement malware and programs tailored to steal a computer’s CPU. Such ‘dangerous’ lines of code are hard to discover, so unsuspected victims cannot understand why their computers are overheated, and the response time takes ages. While a computer is working hard during your daily digital routine, hackers make your PC solve difficult mathematical problems to add new blocks to a blockchain and get a reward.
Cryptojacking is rapidly gaining momentum as the crypto industry is moving toward mass adoption. There are multiple ways to ‘catch’ a virus and get hacked. This is where we kindly remind you to stay safe. All the necessary precautions will be provided below.
How Does Cryptojacking Work?
The digital space evolves, and so do hackers. Web users became more educated in terms of cybersecurity than they were, say, ten years ago. Yet, cryptojackers are quite ingenious and able to infect your device without you even noticing.
The way cryptojacking works is quite plain: a user clicks a link that uploads lines of infected code. The code is activated automatically to literally suck the victim’s computing power resources for hacker’s demands or, in the case of cryptojackers, mining resources.
Cryptojacking via Websites and Emails
The most well-spread method of cryptojacking is Internet advertisements and banners. You are probably familiar with conventional clickable web ads that promise a rich piece of something right now. You are also aware that these are dangerous and might infect your device with rampant malware. However, cryptojackers are smart enough to enslave your computer smoothly and invisibly.
The malicious code is often incorporated into, for example, a website’s WordPress plugin or ads reflected on this website. The owner of a website might not know about the issue, but the code will be spread among users. It hurts both clients and the website’s reputation but enriches cryptojackers.
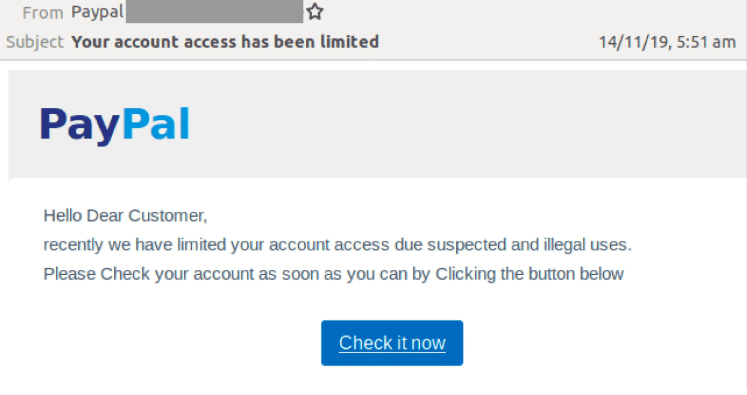
Besides ads, hackers might send emails on behalf of trustable services and companies. The email will probably look unsuspicious and legitimate and contain an attachment or a link that leads to a weird website. Once activated, the link will upload insidious lines of code to a computer. You won’t even notice that something is wrong, but your computer will mine cryptocurrency in the background, leaving you with lower computer productivity and higher electricity costs.
Cloud Cryptojacking
Cloud services are quite convenient when we talk about data storage. However, it is also a perfect target for cryptojacking attacks. They search through a user’s data or files of a particular organization to find breaches and API keys for quick access to cloud servers. Once done, hackers use cloud resources to mine cryptocurrency. A user or an organization, in their turn, wonders why the cloud account bills have increased drastically.
Cryptojacking via Mobile or Desktop Applications
Some applications have been found to be a mask for cryptojacking. In many cases, these applications are downloaded from legitimate app stores and promise to provide some service or function. However, embedded within the code of the app is a cryptocurrency mining script that runs in the background, stealing the victim’s CPU resources. In some cases, the app may also include other malicious functionality, such as stealing personal data or sending premium text messages.

Cryptojacking apps are found on the Microsoft Store: image source
Is Cryptojacking a Crime?
While cryptojacking can be considered a form of theft, it is not necessarily illegal. In many cases, it falls into a legal gray area. For example, if a website uses cryptojacking to generate revenue, the website owner may not be violating any laws. However, if a person uses cryptojacking software to mine cryptocurrency on another person’s computer without their permission, that person may be violating the law. Cryptojacking can also be used for malicious purposes, such as stealing data or infecting computers with malware. In these cases, cryptojacking is definitely illegal and can result in serious penalties.
Good girls and boys choose to get crypto the legal way. Fortunately, we have Changelly Exchange with a user-friendly interface and competitive rates.
Cryptojacking Examples & Malicious Crypto Mining News
According to the SonicWall Cyber Threat Report, there were 66.7 million episodes of cryptojacking in the first half of 2022, which is a 30% increase over the same period in 2021. Based on the research, cryptojacking attacks have increased by 269% in the financial sector.
- The most infamous cryptojacking attack occurred to the largest cryptocurrency miner, Coinhive, in 2018. The service promoted so-called browser mining and allowed websites to get revenue by using the Coinhive script. Websites would no longer place annoying ads but earn extra income. However, cybercriminals modified Conhive scrypt so that it could mine cryptocurrency (Monero) via users’ browsers in the background. This situation led to the closure of Coinhive service in 2019, yet there are still many victims.
- In January 2021, the cybersecurity experts at SentinelOne announced that some macOS computers have long been used by fraudsters for hidden cryptocurrency mining. OSAMiner has managed to evade detection for 5 years!
Malicious software appeared on the network no later than 2015. It was distributed through bootleg games and other programs, including League of Legends and Microsoft Office for Mac. OSAMiner primarily targeted China and the Asia-Pacific region. - In October 2022, Bitdefender discovered that the perpetrators of the most recent cryptojacking campaign were utilizing a known DLL sideloading vulnerability in OneDrive by creating a bogus secur32.dll file. The phony secur32.dll downloads free Bitcoin mining software and injects it into genuine Windows processes once it has been loaded into one of the OneDrive processes. DLL side-loading has the potential to be utilized for the distribution of spyware or ransomware, but the Onedrive sideloading campaign only focused on cryptojacking.
How to Detect Cryptojacking Malware on Your Computer or Mobile Device
So, how can you find out if there is cryptojacking software on your device? Well, thankfully, it’s not that hard.
Cryptojacking code consumes a lot of computing power. Although that’s bad news for the victim’s computer, it at least makes it relatively easy to detect.
Monitor Performance
As we have just mentioned, cryptojacking consumes a whole lot of computing power. Because of that, one of the easiest ways to detect if your device loads crypto mining code every time you turn on the monitoring performance.
Use in-built software like the Performance Monitor for Windows or the Activity Monitor on Mac to monitor your central processing unit (CPU) usage – cryptojacking code can steal CPU processing resources.
Abnormal overheating is another sign that can mean there’s cryptomining code on your PC or mobile phone.
If your computer or phone alerts you that its performance has been slow lately, or you notice it yourself, there’s a possibility that there is cryptomining code on your device.
Scan for Malware
Use reliable antivirus software to scan your device for malware if you notice something seems to be off about your computer’s or mobile phone’s performance.
If you are enjoying this article, and you would like to stay updated on the crypto world’s latest news, don’t forget to subscribe for our weekly email newsletter.
How to Prevent Cryptojacking
Once you detect that there’s uninvited cryptomining going on on your device, it won’t be that hard to get rid of the cryptojacking script and terminate the mining process. In case of an in-browser JavaScript attack, just close the tab that is running the script. If one of your extensions is the issue, update them all and purge unneeded ones.
However, no matter whether you have experienced a cryptojacking attack in the past or not, the most important thing you can do is prevent it from ever happening again in the future. Although it is impossible to fully safeguard yourself against it, there are some steps you can take to minimize the chance of being a cryptojacking victim.
Antivirus Software
Installing reliable antivirus software is something everyone should do regardless of whether it’s cryptojacking they want to protect themselves against or not. Malware, just like biological viruses, only ever keeps on evolving and adapting to our defenses, so you should make sure to get software that gets updated regularly and accounts for the latest cryptojacking trends.
Browser Extensions Designed to Block Cryptojacking Scripts
Most cryptojacking scripts are hidden on websites, so one of the best ways to protect yourself against them is using browser extensions that can either detect them or block such scripts completely. You should also make sure that all extensions in all your web browsers are updated to the latest version and that you are not running any weird or suspicious extensions that you do not need.
Ad Blockers
In-browser cryptojacking scripts are often delivered through web ads, so getting an Ad Blocker can help to protect your device from crypto mining code.
Disable JavaScript
Disabling JavaScript is one of the best things you can do to protect yourself against cryptojacking. However, it will also disable various features on the websites that you may visit. Because of this, disabling JavaScript is an extreme measure that you should take only if you’re really worried about becoming a victim of cryptojacking or if you visit a lot of suspicious websites.
How Prevalent Are Cryptojacking Attacks?
According to a cybersecurity company Aqua Security, 95% of attacks on compromised cloud servers are aimed at the hidden mining of cryptocurrencies. There are three reasons why cryptojacking is common: it does not require elevated permissions, is platform-independent, and rarely runs antivirus software. The code is often small enough to be discreetly inserted into open source libraries and dependencies that other platforms rely on. It can also be configured to tunnel depending on the device, and it can also use flavors of encrypted DNS to keep it quiet. Cryptojacking can also be built for almost any context and in any language like JavaScript, Go, Ruby, Shell, Python, PowerShell, etc.
Final Thoughts
Anyone can be affected by a cryptojacking attack. However, security measures taken on time might protect you from malware intervention. If you notice any abnormal activity within your device, it is a red alert for you to act fast. Changelly takes strong security precautions in order to provide you with instant and secure crypto swaps and purchases. Get access to over 400 digital assets and exchange crypto at the best rates. Buy cryptocurrency with your credit card (Visa, Mastercard), bank transfer, or Apple Pay. Stay safe.
Disclaimer: Please note that the contents of this article are not financial or investing advice. The information provided in this article is the author’s opinion only and should not be considered as offering trading or investing recommendations. We do not make any warranties about the completeness, reliability and accuracy of this information. The cryptocurrency market suffers from high volatility and occasional arbitrary movements. Any investor, trader, or regular crypto users should research multiple viewpoints and be familiar with all local regulations before committing to an investment.