Since 2009 when Bitcoin appeared, the crypto sphere has changed a lot. Together with the well-known algorithms Proof of Work and Proof of Stake, other mechanisms with alternative methods for achieving consensus within the blockchain were proposed. The above-mentioned algorithms have a few drawbacks, which is why the Proof of Authority algorithm appeared.
Today, Proof of Authority is currently being implemented as a more efficient alternative, as it is capable of performing much more transactions per second. However, its benefits are not confined by the speed only. What are the peculiarities of PoA technology? This guide is here to explain the principles of the PoA network.
Table of Contents
What is a Proof of Authority?
Proof of Authority (PoA) is a reputation-based consensus algorithm that provides a practical and efficient solution for blockchains (especially private ones). The term was coined by Ethereum co-founder and former technical specialist Gavin Wood in 2017.
The consensus PoA algorithm uses the value of identifiers, which means that the block validators do not create coin stakes, but instead have their own reputation. Consequently, PoA blockchains are protected by validation nodes that are considered to be trustworthy.
The Proof of Authority model is based on a limited number of block validators, and this is what makes it a scalable system. Blocks and transactions are checked by pre-approved participants who act as moderators of the system.
Here is a great explanation of the PoA by Oracles.org company:
The coherent PoA algorithm can be applied in various scenarios, and they are considered a high-value option for logistics applications. For example, when it comes to supply chains, PoA is considered a more efficient and reasonable solution.
How does it work?
Validators run software to put transactions in blocks. The process is automated and does not require validators to constantly monitor their computers. This, however, requires maintaining the computer (admin site) in good condition.
In order to be elected as a validator, a user should comply with three basic conditions:
- The identity must be formally verified on the network with the possibility of cross-checking the information in a public domain.
- Obtaining the right to be elected as a validator who is authorized to confirm earned and evaluated blocks should not be easy (for example, a potential notary is required to obtain a state notarial license).
- There should be full consistency in the checks and procedures for establishing authority.
With the PoA algorithm, people get the right to become validators, so they have an incentive to maintain the position that they received. To avoid spoiling their reputation, validators are motivated to maintain a normal transaction process. Thus, most users value their hard-earned role of a validator.
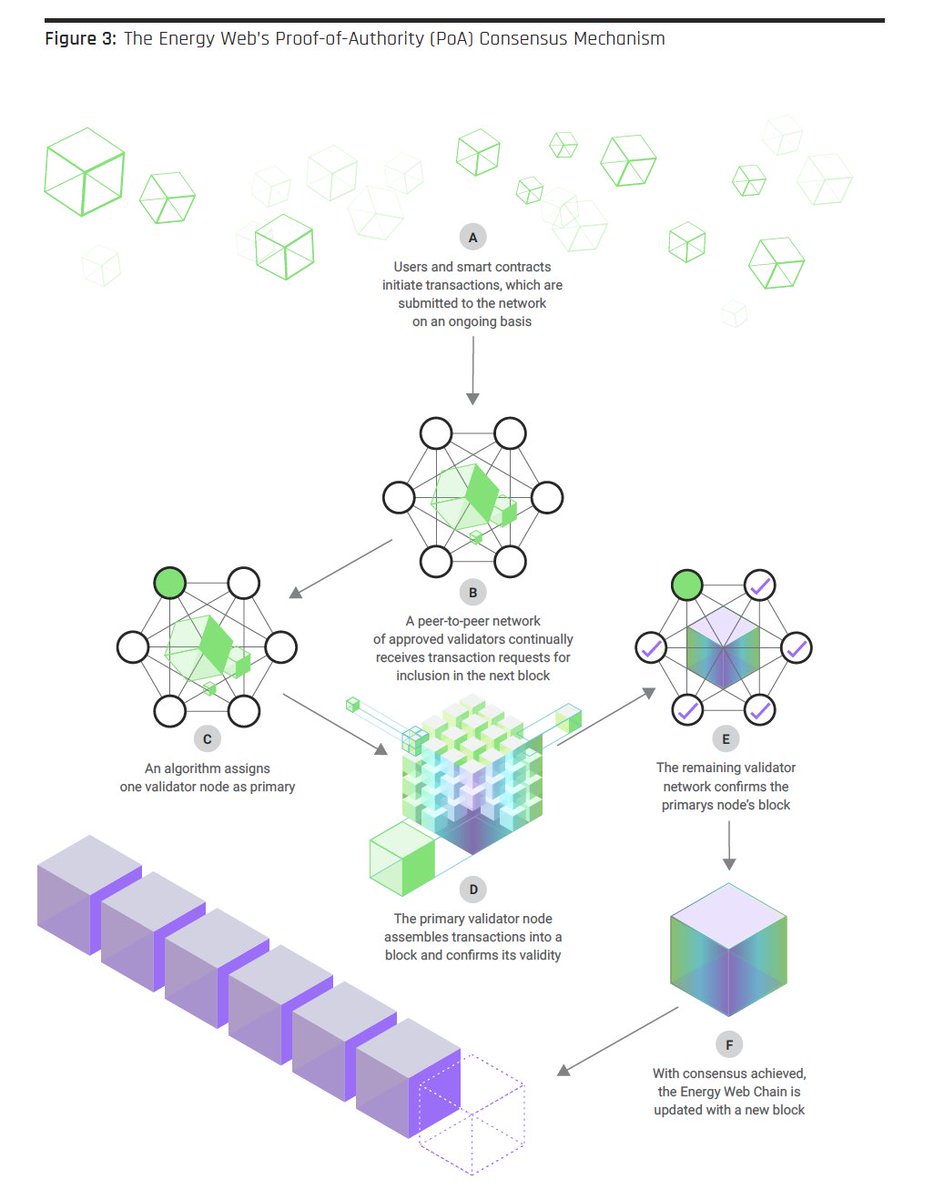
Pros and cons
Yes, this consensus algorithm is not devoid of drawbacks. Let’s observe the main pros and cons of technology:
| Pros | Cons |
| Using PoA eliminates the possibility of an attack since the validators are checked at the stage of obtaining authority and are reliable. | With the use of PoA, decentralization is not possible since a limited circle of people can participate in block validation |
| It’s an energy-efficient solution compared to other consensus mechanisms | Although PoA can be used in public blockchains, it is usually applied in private blockchains requiring permission |
| Fast transaction processing | Reputation cannot always keep participants from malicious actions. If the reward for fraud is more valuable than the authority, a participant can harm the system. |
| A new block is created in just 5 seconds, the fees are extremely low, and network scaling can occur horizontally, combining several networks into one. |
How the mechanism of authority works?
The authority of a miner can vary from 0% to 100%. Initially, conditions for each validator are the same. That is, if you become a validator, you can have a greater influence on the network than some major bank. Everything is achieved on the basis of the scope of work and the degree of authority of the remaining miners. Each transaction requires the participation of at least two nodes with greater authority than the initial node. Example: if the initial influence is 40%, then the other two should have 40% +.
Thus, no mining is possible with the Proof of Signing authority. Approved influential participants are involved in transactions and blocks, which means that their capacities are used to confirm all operations. This can significantly reduce network maintenance costs. In comparison with PoW and PoS mining, Proof of Authority is more energy-efficient because PoA network mining is not possible.
Which blockchains use PoA?
The Proof of Authority model allows companies to maintain their confidentiality by taking advantage of blockchain technology. When it comes to Proof Of Authority, Ethereum is the best example of how technology can be leveraged. Proof-of-authority is not widely used in practice, although it has one of the most advanced work models. This protocol is most applicable to private blockchains since there can essentially be no disagreements within the system. This term was first introduced by Gavin Wood, co-founder of Ethereum and Parity Technologies.
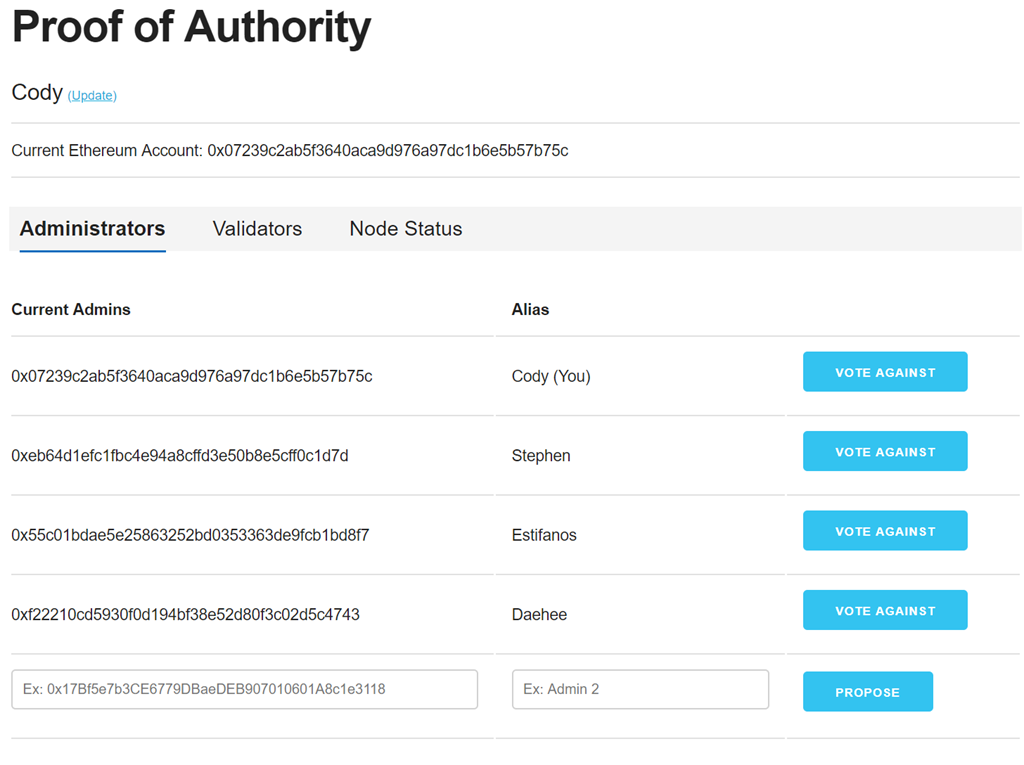
Another case is Ethereum Proof-Of-Authority on Azure. In a nutshell, the Azure platform provides solutions for private networks with a system that does not require its own currency, such as gas from the Ether, since there is no need for mining.
Also, according to the latest information, Pavel Durov plans to use the Proof-of-authority for mining the internal Telegram cryptocurrency called Gram.
Other blockchains with Proof Of Authority coins are POA.Network, Ethereum Kovan testnet, and VeChain.
Why PoA is superb to PoW?
The PoW consensus algorithm used by Bitcoin is the most reliable and secure to date. However, it is not scalable. Bitcoin, as well as other PoW-based blockchains, have limited transaction per second (TPS) performance. This limitation is conditioned that Bitcoin relies on a distributed network of nodes that need to reach consensus and agree on the current state of the blockchain. This means that before a new transaction block is confirmed, it must be verified and approved by most network nodes. Therefore, the decentralization aspect of Bitcoin not only provides a safe and trusting economic system but also limits its potential for wider use.
Regarding the number of transactions per second, the Proof of Stake blockchains usually shows better performance than Bitcoin. However, the difference is not very impressive, and PoS networks also failed to solve the scalability problem. This is where Ethereum Proof Of Authority came in handy.
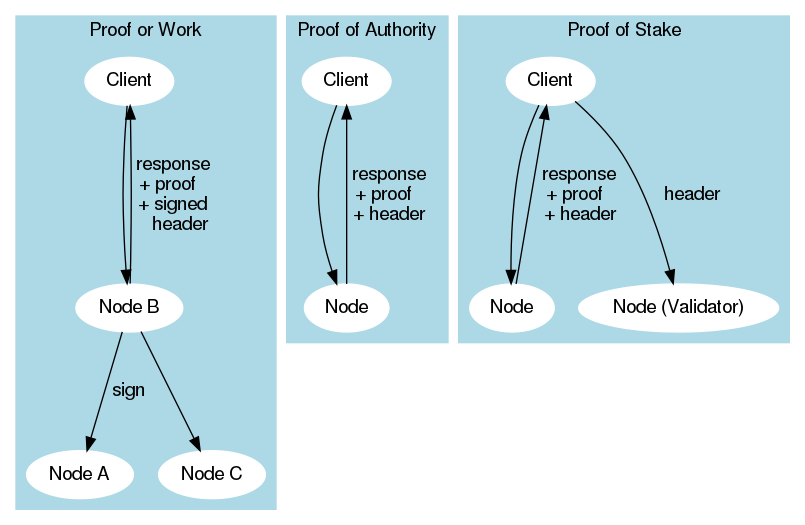
Proof of Authority vs Proof of Stake
Some people think that PoA is a modified PoS that uses identity instead of coins. Due to the decentralized nature of most chain networks, PoS is not always suitable for certain enterprises and corporations. In contrast, PoA systems may represent the best solution for private blockchains, since its performance is significantly higher.
Consensus Terms in the Proof of Authority
Although conditions may vary from system to system, a coherent PoA algorithm depends on:
- Active and trustworthy individuals (validators who must identify themselves);
- The difficulty of becoming a validator: the candidate must be ready to invest money and put his reputation on the line. A tough process reduces the risk of selecting questionable validators and stimulates long-term commitment;
- Validator Approval Standard: The method for selecting validators should be the same for all candidates.
The essence of the reputation mechanism is confidence in the identity of the validator. It’s not a simple process, and weak players are eliminated. Finally, this ensures that all validators go through the same procedure, which guarantees the integrity and reliability of the system.
Limitations
The perception of the PoA mechanism is the rejection of decentralization. Thus, we can say that this model of the consensus algorithm is just an attempt to make centralized systems more efficient. Although this makes PoA an attractive solution for large corporations with logistical needs, it causes some fluctuations, especially in the cryptocurrency area. PoA systems have high bandwidth, but aspects of immutability are questioned when things like censorship and blacklisting can be easily implemented.
Another common critical issue is that the identity of PoA validators is accessible to everyone. The argument against this is that only recognized players are able to hold this position and they will always strive to become a validator (as a publicly known participant). However, knowing the identity of the validator can potentially lead to manipulation by third parties. For example, if a competitor wants to disrupt a PoA-based network, they might try to influence a publicly known validator to dishonestly compromise the system from the inside.
Conclusion
There is no ideal consensus mechanism – each of the existing ones has some drawbacks. PoW and PoS lack scalability. It is well known that decentralization is highly valued by the cryptocurrency community, but PoA, as a consensus mechanism, sacrifices decentralization to achieve high throughput and scalability. The innate features of PoA systems are a stark contrast to how blockchains still function. However, PoA is superb technology and cannot be ignored as the emerging blockchain solution, which may be well suited for private blockchain applications